Understanding security testing essentials is crucial in today’s digital world. As cyber threats evolve, applications become more vulnerable to attacks. Developers and testers must ensure that security is built into the software development process from the very beginning.
In this article, you’ll learn how to identify vulnerabilities, explore different types of security tests, and apply techniques to fix common issues.
Why Security Testing Matters
Security testing protects your application from unauthorized access, data breaches, and cyberattacks. Without it, sensitive user data could be exposed. Moreover, compliance requirements like GDPR, HIPAA, and PCI-DSS demand strong security measures.
Organizations that ignore security testing risk reputational damage, financial losses, and legal penalties. Therefore, implementing security best practices is not optional—it’s essential.
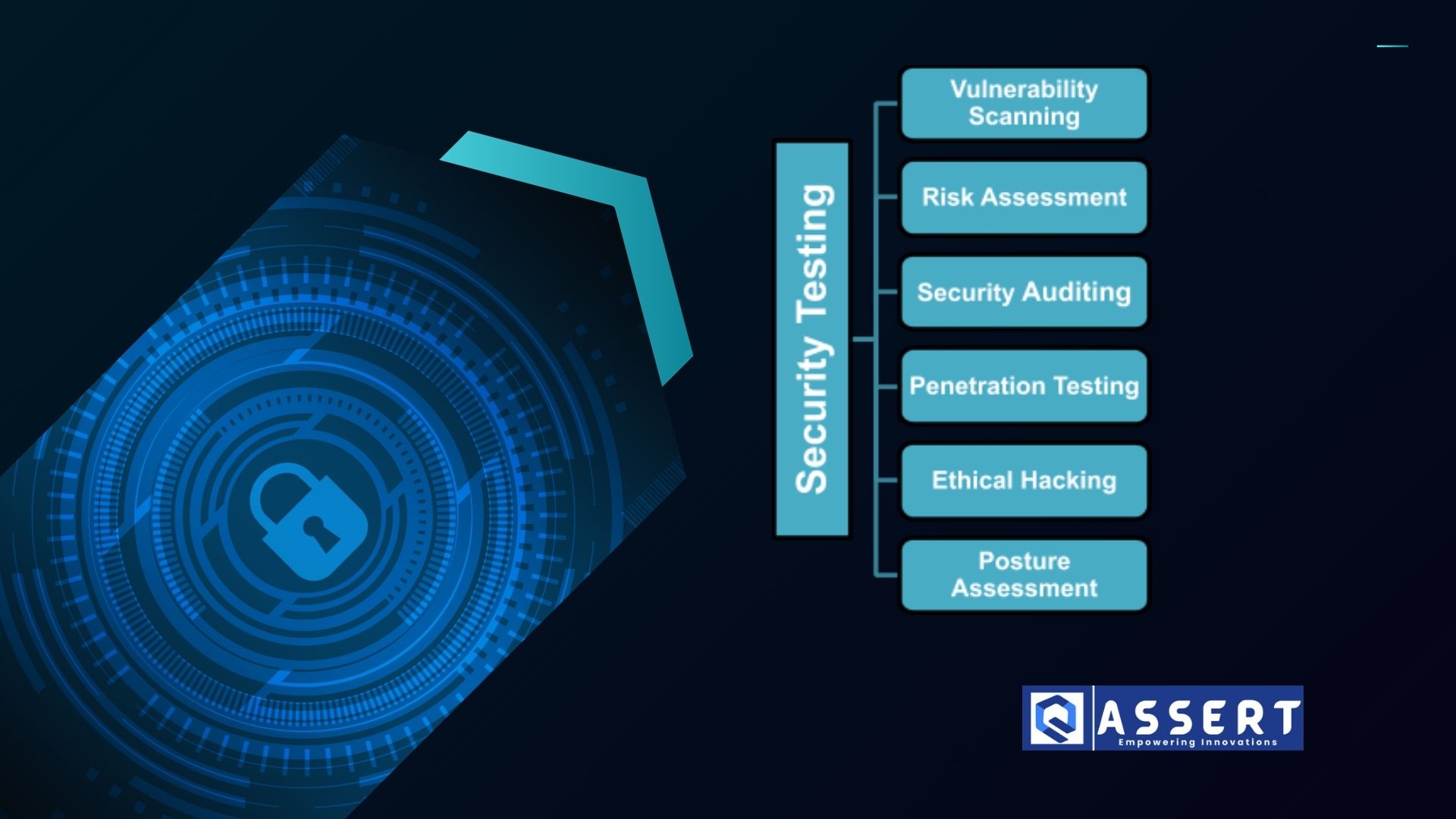
Types of Security Testing
Security testing includes several methods, each serving a different purpose:
-
Vulnerability Scanning – Automatically scans for known vulnerabilities using tools like OWASP ZAP or Nessus.
-
Penetration Testing – Simulates real-world attacks to uncover weaknesses.
-
Risk Assessment – Evaluates security risks and helps prioritize fixes.
-
Security Audit – Reviews code and configurations for compliance and best practices.
-
Ethical Hacking – Involves certified experts mimicking hackers to find flaws before attackers do.
Using a combination of these methods ensures stronger protection.
How to Find Vulnerabilities
To identify security issues effectively, follow these steps:
-
Define your test scope – Decide which systems, APIs, or endpoints need evaluation.
-
Use automated scanners – Tools like Burp Suite and ZAP help uncover issues quickly.
-
Perform manual testing – Combine automated tools with expert insights to detect complex flaws.
-
Analyze source code – Static code analysis tools such as SonarQube highlight risky patterns.
-
Prioritize based on risk – Focus on high-impact vulnerabilities first.
These steps help ensure your security testing is comprehensive and targeted.
How to Fix Vulnerabilities
Finding vulnerabilities is only part of the job. Fixing them effectively requires collaboration between security teams and developers. Follow these best practices:
-
Patch regularly – Keep your software, libraries, and plugins up to date.
-
Use secure coding practices – Validate inputs, encrypt data, and avoid hardcoded secrets.
-
Implement DevSecOps – Integrate security into your CI/CD pipeline.
-
Apply access controls – Limit user permissions and secure sensitive endpoints.
-
Retest after fixes – Ensure vulnerabilities have been resolved by retesting affected areas.
Additionally, educate your teams about secure development to prevent future issues.
Best Tools for Security Testing
Some of the most popular tools for testing and fixing vulnerabilities include:
-
OWASP ZAP: Free, open-source web app scanner.
-
Burp Suite: Advanced web vulnerability scanner.
-
Nessus: Network vulnerability scanning.
-
SonarQube: Static code analysis.
-
Snyk: Finds and fixes open-source security issues.
These tools help improve your software’s security posture and prevent attacks.
Conclusion
To summarize, mastering security testing essentials is key to protecting your software and users. Start by identifying vulnerabilities, use proven testing methods, and apply fixes promptly.
Security is not a one-time activity. It should be an ongoing part of your development cycle. By integrating tools, training, and best practices, you can reduce risks and deliver safer applications.
To learn more, visit the OWASP Foundation for resources, tools, and community support.